Identify Where Sensitive Data Is and Why It Is Sensitive
Gain Greater Visibility Over The Contents Of Your Files As Lepide Automatically Scans And Classifies PII, PHI, PCI, IP And Other Regulatory-Related Data. Lepide’s Data Discovery and Classification Software Helps Provide You With More Context About Your Most Sensitive Data, So You Can Easily Identify Potential Exposure Areas And Implement The Right Access Controls. See How Many of Your Files Contain Sensitive Data, Where They Are Distributed, What Kind of Data You Have, and More.

Improve Data Security
Address which data should be the focus of your security strategy, which data is potentially overexposed, which data applies to compliance regulations, and legacy data.

Easier Compliance Response
Most compliance regulations require you to know exactly where your sensitive data is located so that you can easily meet GDPR requirements such as access requests and the right to be forgotten.

Remove False Positives
False positives are a common problem faced by many classification tools. Proximity screening allows you to filter out false positives from your screening to improve the accuracy of your classification.
How Data Classification Works
Incremental Scanning; After the initial discovery and classification scan, data can be progressively classified at the point of creation/modification to give you a scalable solution that works quickly and efficiently. Wide File Types; You can scan a wide range of different file types including word documents, text documents and excel spreadsheets to find where your sensitive data is. Prioritize Data by Risk; Categorize and score data based on the risk value of the content so you can focus your user behavior analytics and permissioning strategies on the most important data.

Giving Context to Data Classification
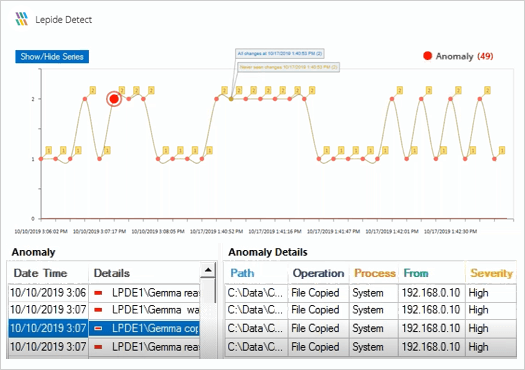
Having more context around which classifications your data falls into allows you to more easily detect suspicious or unwanted user behavior.
Unauthorized permission changes, abnormal user behavior, multiple failed access attempts and other signs of a data breach can be captured, reported and alerted in real-time.
If the worst happens, you can quickly determine the severity of a breach by identifying what type of data is involved.
Use Data Classification to Determine Appropriate Access Rights
Easily identify owners of sensitive files to make better decisions about who can access your sensitive data.
Proactive classification allows you to work towards a least-privilege model where users only have access to the data they need to do their jobs.

Using Data Classification to Improve Data Security
Having more context around which classifications your data falls into allows you to more easily detect suspicious or unwanted user behavior.
Unauthorized permission changes, abnormal user behavior, multiple failed access attempts and other signs of a data breach can be captured, reported and alerted in real-time.
If the worst happens, you can quickly determine the severity of a breach by identifying what type of data is involved.

