Data Access Governance Software
The modern attack surface is expanding every day as employees join, leave, and move roles within the business. This often causes access rights to sprawl out of control, leading to increased risk. Our Data Access Governance software enables you to identify where your sensitive data is, see who has access to it, how access is being granted, spot users with excessive permissions, and monitor user behavior.

Classify Sensitive Data
Determine where your sensitive data is and why it is sensitive. Tag, classify and score that data based on the content.

Stop Unauthorized Access
Find out who has access to your data and how it was granted, and reverse excessive permissions from within the solution.

Monitor User Behavior
Find out what your users are doing with your data and whether the changes they are making are affecting your security.

Detect Anomalies
Get instant notifications when users are making changes they have never made before, including single point anomalies.

Detailed Pre-Set Reports
Hundreds of pre-set reports related specifically to security and data access governance challenges.

Real Time Alerting
Get alerts delivered straight to your inbox or mobile when potentially harmful changes are being made.
Ensure Effective Data Access Governance
Enhance your Data Access Governance (DAG) program with immediate visibility over changes to your critical data and surrounding systems.
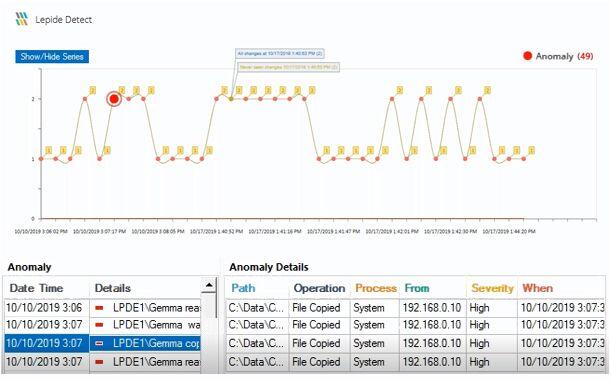
Know What Your Users Are Doing
With interactive tiles, you get a consolidated view of daily interaction activities and user behavior around your most sensitive data. You can also see privilege changes such as Security Group changes, Mailbox Permission Changes and file/folder permission changes. Easily drill down into the tile to reveal full, detailed reporting on individual interactions and privilege changes.
Real-Time Alerts for Changes
Our dashboards are updated in real time, summarizing when risk is actually happening. This means you have the ability to configure contextual alerts based on what poses the biggest threat to your data and the critical systems that manage access to it. You can receive these alerts directly into LiveFeed to react immediately when a new threat is detected. All alerts can be color-coded by criticality, so you can easily identify visually which alerts are high priority.
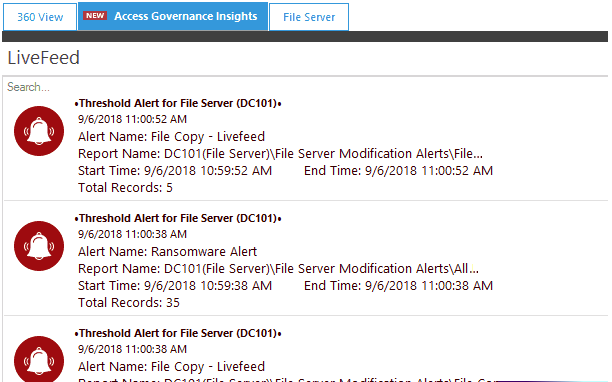
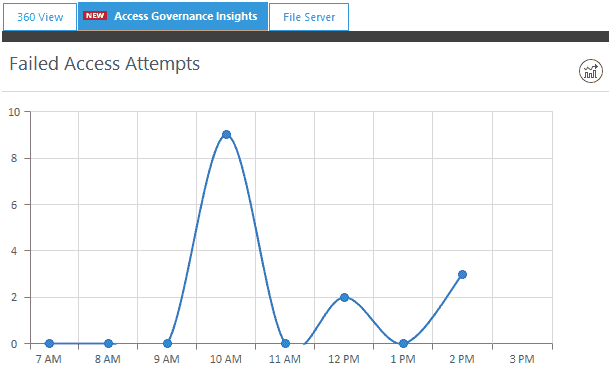
An Overview of Failed Access
With visual representations of both failed logins and failed access attempts to your systems and data, you can quickly determine if users are attempting to access data for which they do not have privileges. Failed logins and access attempts can indicate a potential security breach or brute force attack anywhere on the network. Both graphs are fully interactive, so you can perform detailed analysis at any given time to get to the finer details of these potential security threats.
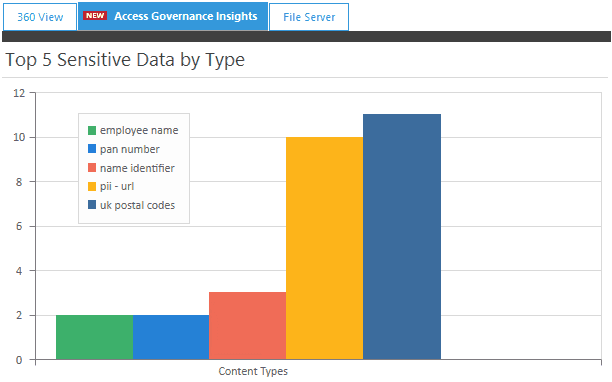
Classifying Sensitive Data by Type
In this interactive summary, we are able to get a holistic view of the total number of files containing your most sensitive data. Depending on how you label and categorize your data, you will have an accurate representation of how many sensitive files reside in your unstructured data. From this vantage point, you can directly drill down into a report detailing the exact location of sensitive files and implement appropriate security measures for any business, with data itself being our most valuable asset.
Reduce Your Potential Attack Surface
Inactive user identities pose a real threat to any organization if they are not properly monitored or managed. These inactive accounts can be targeted by attackers or malicious actors to perform administrative tasks or even steal data that is not legitimately recognized as authenticated users on the network. In this overview, you can get a realistic risk presentation of your legacy users and click to view a detailed report on inactive accounts. Within the Lepide Data Security Platform, you can automate actions for handling accounts, such as resetting the password, deactivating, archiving and even automatically deleting accounts after a certain period of inactivity.

