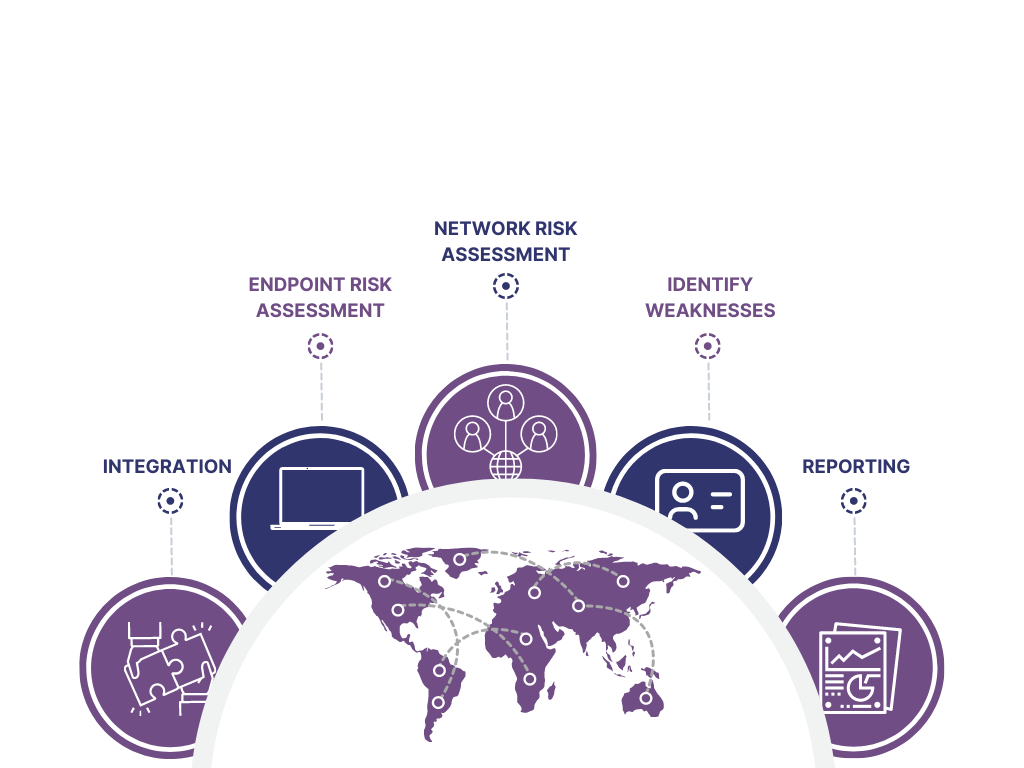
Endpoint Risk Assessment
Evaluate the security posture of individual endpoints, identify vulnerabilities, and mitigate risks by conducting endpoint-specific scenarios.
Network Risk Assessment
Continuously monitor the network security posture using networkspecific attack scenarios, produce trend reports, and improve network security posture.
Identify Weaknesses
Identify potential weaknesses in an organization’s cybersecurity infrastructure and provide actionable insights for improvement purposes.
We Care About Privacy & Secure Your Data
ThreatBleade, provides the best Breach & Attack Simulation service for its customers with its expert team with more than 15 years of experience team. It approaches your system with two perspectives; attacking and defending. It .analyzes your systems from an attacker‘s perspective with its experienced personnel in the red team. Then detects mitigations according to the red team with its experienced personnel in the blue team. Then it combines all of these to provide the best security solution.
* No credit card required
About
ThreatBlade Solutions
Contact us now and we will provide a solution.
Support Email
talk to our agent
Contact us now and we will provide a solution.
Support Email
talk to our agent